Essential Networking Foundations for CompTIA Security+ Success
One way to visualize TCP/IP in action is to follow a simple scenario: You open your web browser at work and navigate to your company’s secure intranet site. What happens under the hood? First, your computer needs the IP address of that intranet site. It will likely use DNS to resolve the domain name (e.g. intranet.company.local) – your PC sends a DNS lookup request (usually a UDP packet to port 53) to your organization’s DNS server. Once DNS replies with an IP (say, 10.1.2.3), your browser initiates a TCP connection to that IP on port 443 (HTTPS). This involves the TCP three-way handshake – a synchronization (SYN) packet, a SYN-ACK from the server, and an ACK – establishing a reliable connection. Over this connection, the TLS handshake then takes place (because it’s HTTPS, adding encryption at the Presentation layer). Now a secure session is established. Your browser sends an HTTP GET request (Application layer) for the intranet homepage. The server’s response travels back as TCP segments, IP packets, Ethernet frames, etc., and your browser finally displays the page. During this whole exchange, multiple protocols worked together: DNS (UDP at Application layer), TCP (Transport), IP (Network), Ethernet and ARP on your LAN (Data Link/Physical). If any step fails – e.g., DNS is down (you can’t resolve the name), or the server isn’t listening on the port, or a firewall blocks port 443 – the page won’t load. This example shows how the TCP/IP suite functions as a coordinated language of the internet, with each protocol playing a role.
In summary, TCP/IP protocols include everything from low-level IP and ARP to high-level HTTP and SMTP. For the Security+ exam, focus on the purpose of key protocols and how they relate to each other. Know that TCP provides reliability (TCP vs UDP: The Main Difference Between TCP and UDP - NetAlly) and UDP provides speed (TCP vs UDP: The Main Difference Between TCP and UDP - NetAlly). Know that IP addresses and routes traffic. And remember that terms like “TCP/IP stack” or “internet protocol suite” essentially refer to this collection of protocols working in unison. A solid grasp of these will make many Security+ questions (and real-world network issues) much easier to tackle.
Ports and Protocols: Key Numbers to Know
If TCP/IP protocols are the languages of network communication, port numbers are like the channels or extensions on which those languages are spoken. Each TCP or UDP port is associated with a specific service or application. For example, web servers typically “listen” on port 80 for HTTP and 443 for HTTPS. The Security+ exam expects you to know many of the common ports and their corresponding protocols, as this is fundamental to securing and monitoring network traffic.
Think of a corporate office building: to visit the Sales department you might dial extension 80, for HR dial 443 – in a similar way, network services use port numbers to distinguish traffic intended for different services on the same host. Below is a handy table of essential ports and protocols often encountered in Security+ study (and real life):
| Port | Protocol (and Purpose) | Description |
|---|---|---|
| 20, 21 | FTP – File Transfer Protocol | Transfers files between systems (TCP). Port 21 is control (commands), 20 is data transfer. Unencrypted by default (use FTPS/SFTP for secure transfer). |
| 22 | SSH – Secure Shell | Encrypted remote login and command execution (TCP). Used for secure administration (replaces Telnet). Also used for SFTP (file transfer over SSH). |
| 23 | Telnet | Unencrypted text communication (TCP). Used for remote login in plaintext – insecure (transmits passwords openly). Generally replaced by SSH (Why is Telnet Insecure? - Pragmatic Paranoia). |
| 25 | SMTP – Simple Mail Transfer | E-mail sending (TCP). Servers use it to send/relay mail. (Secure SMTP often on 587 or 465 with TLS). |
| 53 | DNS – Domain Name System | Converts domain names to IP addresses (and vice versa). Uses UDP for most queries (What Is a Virtual Private Network (VPN)? - Cisco); TCP for large transfers (zone transfers). Critical for network functionality. |
| 80 | HTTP – Hypertext Transfer Protocol | The foundation of the World Wide Web (TCP). Unencrypted web traffic (uses plain text). Should be secured with HTTPS for sensitive data. |
| 110 | POP3 – Post Office Protocol v3 | Receiving email (TCP). Retrieves emails from mail server to client. Unencrypted by default (secure version on 995 or via TLS). |
| 143 | IMAP – Internet Message Access | Retrieving email (TCP). More advanced than POP3 (supports syncing folders). Unencrypted by default (secure version IMAPS on port 993). |
| 389 | LDAP – Lightweight Directory Access | Directory services (TCP/UDP). Querying directories (like Active Directory) for user and resource info. Unencrypted by default; LDAPS (LDAP Secure) on port 636 adds TLS. |
| 443 | HTTPS – HTTP Secure (with TLS) | Encrypted web traffic (TCP). Uses TLS/SSL to secure HTTP. This is what makes your padlock icon in the browser. Protects data in transit from eavesdropping. |
| 445 | SMB – Server Message Block | Windows file sharing (TCP). Used for sharing files, printers (also known as CIFS on modern systems). Operates directly over TCP (older SMB/NetBIOS used ports 137-139). |
| 3389 | RDP – Remote Desktop Protocol | Remote desktop access (TCP/UDP). Used to remotely control Windows machines (graphical interface). Often restricted to internal networks or VPN due to security. |
These are not all the ports you might encounter, but they represent some of the most common ones. It’s a good idea to memorize the port numbers and services – not just for the exam, but because as an IT professional you’ll constantly run into them. For instance, if a security scan shows that port 23 is open on a server, a red flag goes up because that means Telnet (insecure) is running – you’d likely want to disable that and use SSH (22) instead. In fact, a common Security+ question may ask something like “Which port number is used by SSH?” or present a scenario: “An admin wants to allow secure remote server management and file transfer, which protocol and port should they enable?” (Answer: SSH on 22, since it provides secure shell and can tunnel SFTP).
Let’s put this into a corporate context for better understanding. Scenario: You’re a network security administrator at a company. You are configuring the firewall and need to allow employees to access the company’s internal website and email server from their homes. The internal website runs on HTTPS (443), and the email server uses IMAPS (993 for secure IMAP) and SMTPS (likely 587 or 465 for secure SMTP submission). You’d ensure the firewall permits inbound connections on those ports to the respective servers, while maybe blocking the old insecure equivalents (like port 80, 110, 25 from outside). Meanwhile, you might totally block ports like 23 (Telnet) or 21 (FTP) from the internet, because you don’t want unencrypted logins or transfers. If remote desktop is needed by IT staff, you might put RDP (3389) behind a VPN or only allow it from certain admin IPs for safety.
From a defensive standpoint, knowing ports helps in intrusion detection too. If you suddenly see traffic on an unusual port – say a workstation trying to communicate out on port 4444 – it could indicate malware (as that port is often used by attacks or backdoors). Similarly, an attacker performing a port scan is essentially knocking on all the port “doors” of a server to see which ones are open and what services are running. As a Security+ practitioner, you should recognize the common ports so you can quickly identify potentially malicious or unauthorized services.
In short, ports and protocols go hand-in-hand. Remember the well-known port numbers for key protocols, and understand which ones are considered secure or insecure. This will not only help in the exam (where ports are a popular topic) but also in real-world tasks like configuring firewalls, troubleshooting service connectivity, and analyzing network traffic.
Network Security Concepts: Protecting the Network
Now that we have the networking basics down, let’s pivot to fundamental network security concepts. These are the principles and technologies that help secure data as it travels across networks. We’ll discuss a few core areas: network perimeters and firewalls, intrusion detection and prevention, and secure communications (like VPNs and encrypted protocols). Each concept ties back to the networking foundations we just covered, adding a layer of protection or monitoring to them.
Firewalls and Access Control
A firewall is often the first line of defense in network security. It’s basically a network security device (hardware or software) that monitors traffic and enforces rules about what’s allowed and what’s blocked. In other words, it’s like a bouncer at the club, checking IDs and deciding who gets in. A firewall sits at the junction between networks (often between your internal trusted network and the untrusted internet) and filters traffic based on a defined set of security rules (What Is a Firewall? - Cisco). For example, a rule might allow inbound HTTPS traffic to your public web server but block all other inbound connections; another rule might prevent any internal devices from initiating connections to known malicious IP addresses outside.
Firewalls can operate at different OSI layers. Traditional packet-filtering firewalls inspect headers up through Layer 3/4 (blocking or allowing based on IP addresses, ports, and protocols). More advanced stateful firewalls keep track of connection states (so they can allow return traffic for an established outbound connection, etc.). There are also application-layer (Layer 7) firewalls or proxy firewalls that can inspect the actual content of traffic (e.g., an HTTP proxy that can allow or block specific URLs or scan for attacks in web traffic). For Security+, you should understand the basic firewall types and their purpose: basically, prevent unauthorized access to or from a network. In a corporate scenario, picture the firewall as the guard at your network’s gateway. If an outside hacker tries to reach a database server that’s meant to be internal-only, the firewall’s rules (if configured correctly) will drop that traffic. Likewise, firewalls can be configured to only allow necessary ports – implementing the principle of least privilege (or least access) at the network level.
On top of external (perimeter) firewalls, many organizations also use internal firewalls or segmentation firewalls to further partition network areas (more on segmentation soon). Also, host-based firewalls (like the Windows Defender Firewall on each PC) add another layer by controlling traffic to and from that specific machine. Defense in depth is the game here – multiple layers of filtering make it harder for an attacker to penetrate deeply into the network.
Intrusion Detection and Prevention (IDS/IPS)
While firewalls are great for blocking or allowing traffic based on rules, what about malicious traffic that might not outright violate a simple rule? This is where IDS (Intrusion Detection System) and IPS (Intrusion Prevention System) come into play. These systems monitor network traffic for signs of attacks or unauthorized behavior. An IDS is like a security camera – it watches and alerts. An IPS is like a security guard – it can intervene to block the threat.
An Intrusion Detection System monitors network traffic for suspicious patterns, such as known attack signatures or abnormal usage, and then generates alerts if something is found (Intrusion Detection | PDF | Malware | Security - Scribd). For instance, an IDS might watch for a known malware signature in network packets or detect if someone is port-scanning your servers. Once it detects something, it will log it and alert administrators, but it won’t automatically stop it (it’s “detection” only). This could be a network IDS (NIDS) placed at a strategic point in the network (like just inside the firewall), or a host-based IDS (HIDS) running on individual servers to monitor local events.
An Intrusion Prevention System does the same monitoring, but can also take action to block or prevent the detected malicious activity. In practice, many modern systems are IDS/IPS combos that can operate in detection or prevention mode. For example, if an IPS detects a SQL injection attack in web traffic, it might drop those packets, effectively shielding the web server from that attack. If it sees an IP address performing a brute-force login attack, it might dynamically block that IP for a period of time.
From an exam perspective, remember the difference: IDS = alert, IPS = alert + block (Can IPS system be used as IDS and vice versa) (IDS vs. IPS: Definitions, Comparisons & Why You Need Both | Okta). Also know that an IPS, because it actively interferes, usually sits in-line with traffic (all traffic passes through it so it can stop bad packets in real time), whereas an IDS might be out-of-band (receiving copies of traffic, like via a SPAN port on a switch, to analyze). In corporate scenarios, IDS/IPS are crucial for catching things a firewall might miss. For example, if an attacker somehow slips a connection through the firewall (maybe over port 443 which must be open for web), the IDS/IPS can inspect that traffic for known malicious content (like an exploit or trojan communication) and raise the alarm or block it. You might configure an IPS to block certain patterns outright (like an attempt to exploit a known Windows SMB vulnerability), whereas an IDS could be used in a monitoring-only mode to collect data on attacks for analysis without risking blocking legitimate traffic.
Secure Protocols and VPNs
Another fundamental concept is using secure protocols to protect data in transit. We saw earlier how protocols like SSH and HTTPS use encryption. A big part of network security is ensuring that if someone intercepts your network traffic, they can’t make sense of it. The use of encryption (mostly via TLS these days) turns protocols into their “secure” versions: HTTP -> HTTPS, Telnet -> SSH, FTP -> FTPS/SFTP, LDAP -> LDAPS, etc. As a Security+ candidate, you should recognize which protocols are secure and which aren’t. For instance, Telnet sends everything (including passwords) in plaintext, which is why it’s considered insecure and deprecated (Why is Telnet Insecure? - Pragmatic Paranoia). SSH was introduced as a secure replacement – it encrypts the entire session. Similarly, older protocols like FTP, POP3, IMAP did not encrypt credentials or data, but now we use FTPS/SFTP, POP3S, IMAPS or simply wrap those in TLS to secure them. Even seemingly innocuous services like DNS have secure versions (DNS over TLS, DNSSEC) to prevent spoofing or eavesdropping. For the exam (and best practice), the rule of thumb is: whenever possible, use the secure version of a protocol. If you see something like Telnet or HTTP in an environment, that’s a weakness to address.
Now, VPNs (Virtual Private Networks) deserve special mention. A VPN is a technology that allows you to create a secure, encrypted tunnel over an untrusted network (like the Internet) (What Is a Virtual Private Network (VPN)? - Cisco). Companies use VPNs to let remote employees securely connect to the internal network from home, or to connect branch offices together over the internet. When you connect through a VPN, it’s as if your computer becomes part of the office network, but all the traffic between your computer and the office is encrypted (typically with strong protocols like IPsec or TLS). So even if someone intercepted the traffic, they’d just see gibberish. Security+ covers VPN concepts such as IPsec (a suite of protocols to secure IP communications – often used in site-to-site VPNs) (What is IPsec? | How IPsec VPNs work - Cloudflare) and SSL/TLS VPNs (often used for client VPNs). A classic scenario: You’re at a coffee shop and need to access internal company files – you fire up your VPN client, it encrypts all your outgoing traffic to the company’s VPN gateway. From the coffee shop’s perspective (or a hacker sniffing the Wi-Fi), all they see is encrypted data between you and your company, which protects against data theft or session hijacking.
Another angle of secure communications is ensuring authenticity and integrity. Protocols like HTTPS not only encrypt but also verify the server’s identity via certificates, helping to prevent man-in-the-middle attacks. When implementing network services, enabling features like certificate-based authentication, MFA (multi-factor authentication) for remote access, and using protocols like SNMPv3 instead of SNMPv1 (because v3 supports encryption and authentication) are all part of network security best practices.
To tie these concepts together: Imagine an employee, Alice, needs to manage a server remotely. The insecure way: enable Telnet (port 23) to that server – anyone spying could steal the credentials and infiltrate. The secure way: use an SSH connection (port 22) – now the login and session are encrypted. Further secure way: require that Alice first VPN into the corporate network, then SSH to the server – adding another layer so that even the initial connection is in an encrypted tunnel and you have an extra authentication step for the VPN. Each layer (VPN, then SSH) reduces the attack surface by ensuring the data is confidential and the access is authenticated strongly.
In summary, network security concepts at this foundational level boil down to: use tools to control who can access the network (firewalls), watch for any bad behavior (IDS/IPS), and protect data as it travels (encryption/VPNs). If you grasp those ideas, you can apply them in various combinations to secure different scenarios.
Secure Network Design: Layering Your Defenses
Building on the concepts above, secure network design is about architecting your network in a way that inherently reduces risk and impacts of attacks. It’s not just one product or one setting, but rather how you organize and arrange the network’s components and zones. Two big elements here are network segmentation (including DMZs) and redundancy/availability planning. Think of secure design as the blueprint that makes a network both hard for attackers to penetrate and resilient in the face of failures.
Network Segmentation and DMZs
Network segmentation means dividing your network into zones or segments, each isolated or filtered from the other, based on security needs. Instead of one flat network where every device can reach every other device directly, you create boundaries. This is a bit like having separate rooms or safes for different sensitive items, rather than one big warehouse. The idea is to reduce the attack surface – even if an attacker compromises one segment, they can’t easily jump to all others (What is Network Segmentation? | CrowdStrike). Segmentation can be achieved with internal firewalls, VLANs (Virtual LANs), subnets, etc.
For example, a common segmentation in enterprise networks is: Internal network vs DMZ vs External. A DMZ (Demilitarized Zone) is a special network segment, usually for public-facing servers (like your company’s web server, email server, VPN gateway, etc.), that is isolated from the internal network (What Is a DMZ Network and Why Would You Use It? | Fortinet). It’s like a buffer zone between the wild internet and your private LAN (What Is a DMZ Network and Why Would You Use It? | Fortinet). The DMZ network provides a buffer between the internet and the private internal network (What Is a DMZ Network and Why Would You Use It? | Fortinet). Typically, a firewall will allow external users to access the servers in the DMZ (since those need to be public), but that DMZ is kept separate so that those servers can’t initiate free communication into the internal network. If a DMZ server gets compromised, the attacker is still stuck in the DMZ and can’t directly reach your crown jewels (internal databases, domain controllers, etc.) without breaking through another layer of security. Meanwhile, internal users can still reach the DMZ services as needed (e.g., your internal database server might accept connections only from the web server in the DMZ, not from arbitrary internet hosts).
There are a couple of common ways to implement a DMZ. One is with a single firewall that has multiple interfaces (one for inside, one for outside, one for DMZ). Another more secure approach is a dual-firewall DMZ: one firewall between internet and DMZ, another between DMZ and internal network. This way, even if one firewall is compromised, there’s a second gatekeeper. Security+ might not require you to design DMZs, but know what the term means: an isolated network for systems that are accessible from an untrusted network, to protect the rest of your network. Web servers, FTP servers, DNS servers that must talk to external clients – these often reside in a DMZ with tight rules.
(File:DMZ network diagram 1 firewall.svg - Wikipedia) Diagram: Example of a single-firewall DMZ network architecture. The firewall (green) has an interface to the public Internet (red), an interface to the isolated DMZ segment (right, with public servers like web “WWW”, email “SMTP”, DNS), and an interface to the internal network (left, with internal client PCs). External users can access the DMZ servers, but the firewall limits any direct access to the internal network (What Is a DMZ Network and Why Would You Use It? | Fortinet).
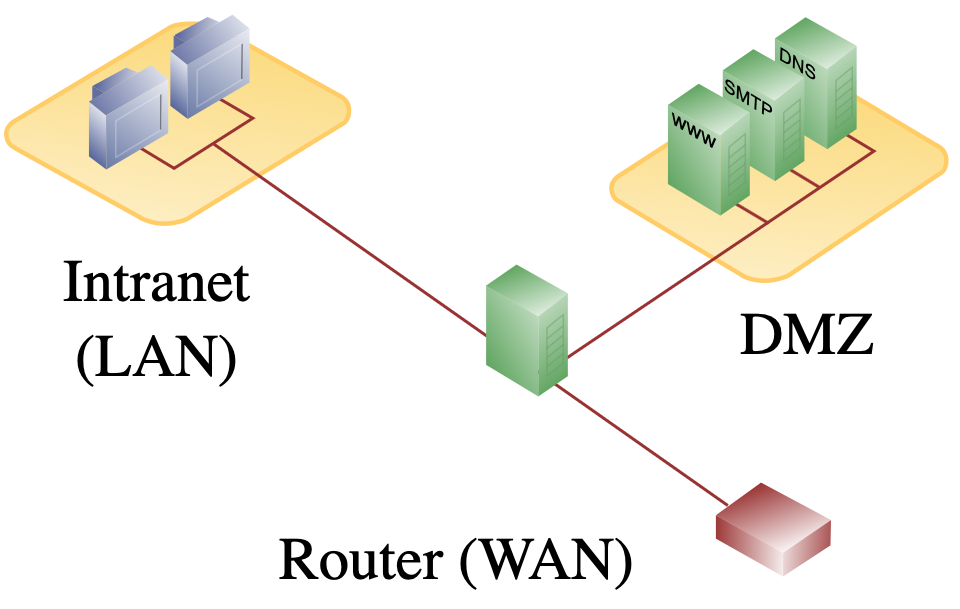
Beyond DMZs, segmentation can also mean separating internal network sections. You might segment by department, by function, or by security level. For instance, put all IoT devices or guest Wi-Fi on a separate VLAN that only has internet access but no access to internal resources. Or segregate the Finance department’s network, which handles sensitive financial data, away from the general employee network. This way if malware infects a user’s PC in one segment, it can’t immediately spread to every other segment. Each boundary (often enforced by a firewall or router ACLs) contains the damage. Network segmentation is a strategy used to segregate and isolate network segments to reduce the attack surface (What is Network Segmentation? | CrowdStrike) – it’s a fundamental concept in limiting how far an attacker or malware can move laterally within a network.
Another concept is the principle of least privilege applied to network design: Only allow necessary communication between segments. For example, if the Accounting VLAN never needs to talk directly to the Research VLAN, then block it. If the web server in DMZ only needs to query the database on one port, don’t allow it to do more than that. The fewer pathways open, the fewer opportunities for an attacker.
To illustrate, consider a hypothetical corporate design: You have an internal LAN for employees, a separate network for servers, a separate one for printers/IoT devices, and a DMZ for external-facing servers. Employees can reach the servers (with authentication) and printers, but printers cannot initiate connections into the LAN (since a hacked printer shouldn’t be able to snoop on PCs). The DMZ servers can talk to internal servers only on specific ports (e.g., the web server can talk to the database server on the database port, nothing else). By implementing this, an outsider who hacks the web server can’t freely roam into HR files, and malware on an employee’s PC can’t directly infect a server without crossing a controlled boundary.
Redundancy and Resilience
Security isn’t just about keeping bad guys out; it’s also about keeping the network running (availability). A secure network design considers single points of failure and tries to eliminate or mitigate them. This means introducing redundancy for critical components: multiple pathways, backup systems, and failover capabilities. After all, an outage due to technical failure can be just as damaging as an attack – and sometimes attackers try to cause outages (DoS attacks) which redundancy can help survive.
Redundant network connections: Remember the mesh topology discussion? In design, you often add alternate links between important devices. For example, two core switches might have two or more cables between them or even a high-availability protocol so if one link fails, the other takes over. Or two routers connecting your site to the internet through two different ISPs – if ISP A goes down, traffic can switch to ISP B. In the context of Security+, this is relevant to business continuity and disaster recovery – a secure design ensures that critical services remain available or quickly recoverable. You might see terms like link aggregation (LACP) for combining multiple links, or Spanning Tree Protocol (ensures loops from redundant switches don’t crash the network), or routing protocols that failover.
Redundant devices: It’s not just links – you can have redundant firewalls (two firewalls in an active/passive pair, so if one fails the other picks up without interrupting traffic), redundant servers (clusters), redundant power supplies, etc. In a secure design, especially for large enterprises or any high-value service, you don’t want a single failure to knock you offline. For example, an online store will have multiple web servers behind a load balancer; if one server fails, the others still serve customers. Similarly, in network design, you might deploy two core switches instead of one, with everything important dual-connected.
High availability and failover are often achieved through protocols and technologies like VRRP/HSRP (for router redundancy), clustering, and load balancing. The Security+ exam might not test the technical minutiae of these, but it will expect you to grasp that redundancy = availability. This ties into the CIA triad (Confidentiality, Integrity, Availability) – availability being a key goal of security. An example question might be scenario-based: “A company wants to ensure their VPN concentrator is always accessible, even if hardware fails. What should they implement?” Answer: redundant VPN concentrators (maybe in a failover pair).
Defense in Depth: Another design principle to mention is layering defenses (which we have implicitly done). Rather than relying on one big wall, you have multiple walls and safeguards. For example, an attacker trying to compromise your network should have to get past a border firewall, then an IDS/IPS watching traffic, then maybe a network access control (NAC) system that checks devices, then deal with segmented networks with internal firewalls, and even if they get to a host, that host has host-based firewall and updated antivirus, etc. At each layer, alarms might go off or countermeasures might stop them. This way no single failure leads to total compromise. In secure design, you assume that some defenses will fail (or be bypassed), so you have others as a safety net.
Finally, consider physical network design aspects: placing critical servers in secure network zones, perhaps separating management interfaces (like out-of-band management networks for switches/routers that only admins can access), and using secure defaults (like all ports closed unless needed). A well-designed network also has monitoring in place – syslog servers, SIEM systems, etc., to aggregate logs from firewalls, IDS, etc., so that if something fishy is happening, your team knows in real time.
In a nutshell, secure network design is about compartmentalizing (so one breach doesn’t sink the whole ship) (What is Network Segmentation? | CrowdStrike) and planning for failure. For the exam, remember terms like DMZ, VLAN, subnetting, segmentation, defense in depth, least privilege, and redundancy. These are your design toolbox. If you get a question about improving a network’s security architecture, think in these terms: “Can I split the network or add a DMZ? Add a firewall or ACL here? Use a VPN for that connection? Provide a backup link or device?” That line of thought will usually guide you to the correct answer.
Conclusion
Networking fundamentals form the backbone of many security decisions and strategies. In this post, we covered the essential networking foundations for CompTIA Security+ – from understanding various network topologies (star, bus, ring, mesh) and why they matter, to mastering the OSI model’s seven layers and seeing how data flows through them. We looked at key TCP/IP protocols like IP, TCP, UDP (and how they differ in reliability vs speed) and supportive protocols like DNS and ARP. We then mapped out the important ports and protocols that every Security+ student (and IT admin) should know by heart, distinguishing between secure and insecure services. Moving into security-specific topics, we discussed network security concepts such as using firewalls to enforce access control, IDS/IPS to detect intrusions, and VPNs and encryption to secure communications. Finally, we pulled it all together with secure network design principles, emphasizing segmentation (like DMZs) to isolate critical assets and redundancy to ensure availability.
The key takeaways can be summed up as follows: Understand how networks are built and operate, so you can better secure them. Each layer of the OSI model and each piece of the network has related security measures (e.g., Physical layer – locks on server rooms; Data Link layer – switching to prevent eavesdropping; Network layer – routing and IP addressing with ACLs; Transport – using secure protocols; Application – patching software, using authentication, etc.). As you prepare for the Security+ exam, keep reinforcing how these networking basics underpin the exam’s security topics. For instance, you’ll find that many exam questions about attacks (like ARP poisoning, or DNS attacks) and defenses (like SSL, or network access control) are best understood if your networking fundamentals are solid.